Introduction
About Kyverno
Kyverno (Greek for “govern”) is a policy engine designed specifically for Kubernetes. Some of its many features include:
- policies as Kubernetes resources (no new language to learn!)
- validate, mutate, or generate any resource
- match resources using label selectors and wildcards
- validate and mutate using overlays (like Kustomize!)
- synchronize configurations across namespaces
- block non-conformant resources using admission controls, or report policy violations
- test policies and validate resources using the Kyverno CLI, in your CI/CD pipeline, before applying to your cluster
- manage policies as code using familiar tools like
gitandkustomize
Kyverno allows cluster administrators to manage environment specific configurations independently of workload configurations and enforce configuration best practices for their clusters. Kyverno can be used to scan existing workloads for best practices, or can be used to enforce best practices by blocking or mutating API requests.
How Kyverno works
Kyverno runs as a dynamic admission controller in a Kubernetes cluster. Kyverno receives validating and mutating admission webhook HTTP callbacks from the kube-apiserver and applies matching policies to return results that enforce admission policies or reject requests.
Kyverno policies can match resources using the resource kind, name, and label selectors. Wildcards are supported in names.
Mutating policies can be written as overlays (similar to Kustomize) or as a RFC 6902 JSON Patch. Validating policies also use an overlay style syntax, with support for pattern matching and conditional (if-then-else) processing.
Policy enforcement is captured using Kubernetes events. Kyverno also reports policy violations for existing resources.
The picture below shows the high-level architecture for Kyverno:
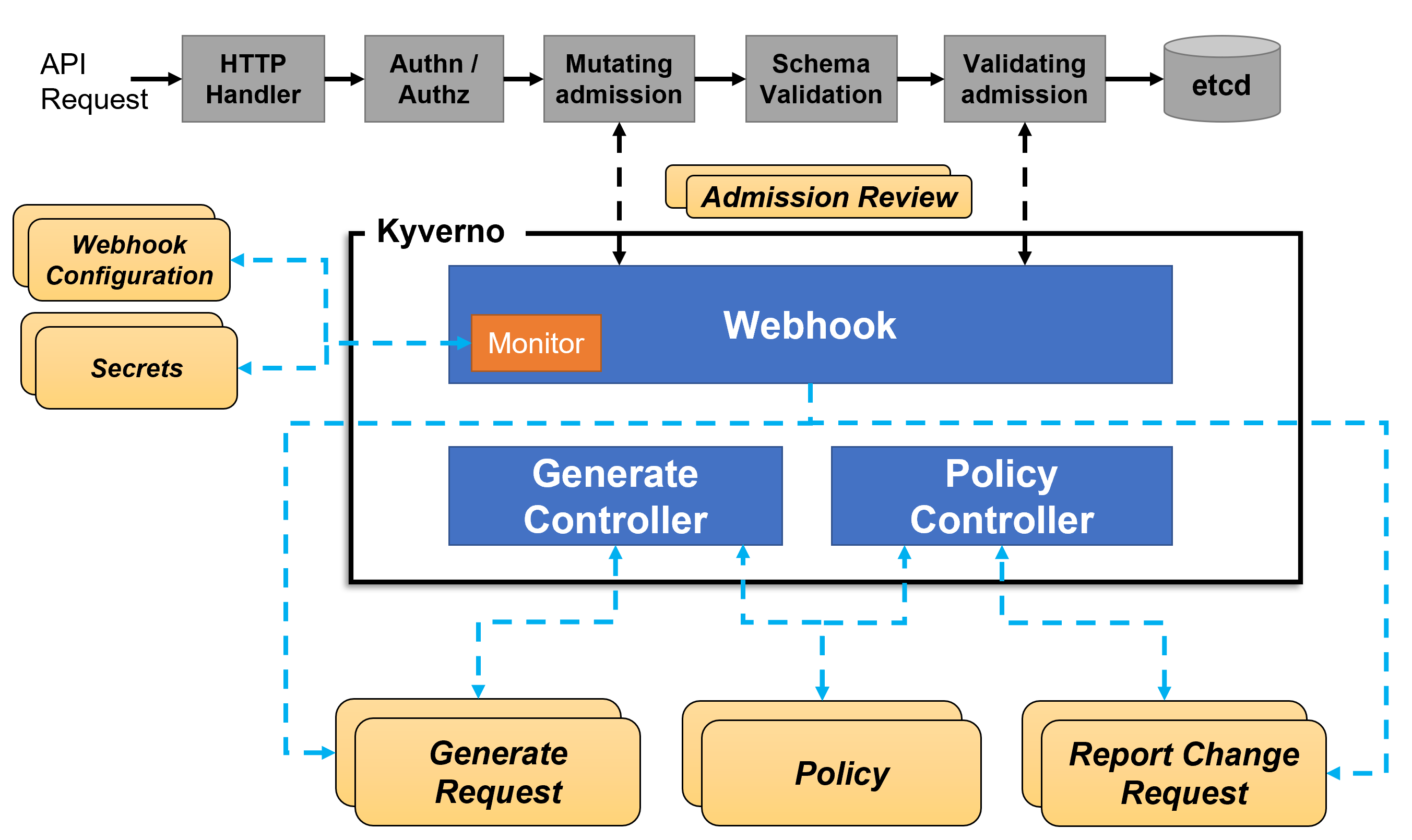
An high availability installation of Kyverno can run multiple replicas, and each replica of Kyverno will have multiple controllers that perform different functions. The Webhook handles AdmissionReview requests from the Kubernetes API server, and its Monitor component creates and manages required configurations. The PolicyController watches policy resources and initiates background scans based on the configured scan interval. The GenerateController manages the lifecycle of generated resources.
Quick Start
This section will help you install Kyverno and create your first policy.
Note
Your Kubernetes cluster version must be above v1.14 which adds webhook timeouts. To check the version, enterkubectl version.
You have the option of installing Kyverno directly from the latest release manifest, or using Helm.
To install Kyverno using the latest release manifest (which may be a pre-release):
1kubectl create -f https://raw.githubusercontent.com/kyverno/kyverno/main/config/release/install.yaml
You can also install Kyverno using a Helm chart:
1# Add the Helm repository
2helm repo add kyverno https://kyverno.github.io/kyverno/
3
4# Scan your Helm repositories to fetch the latest available charts.
5helm repo update
6
7# Install the Kyverno Helm chart into a new namespace called "kyverno"
8helm install kyverno --namespace kyverno kyverno/kyverno --create-namespace
Add the policy below to your cluster. It contains a single validation rule that requires that all Pods have a app.kubernetes.io/name label. Kyverno supports different rule types to validate, mutate, and generate configurations. The policy attribute validationFailureAction is set to enforce to block API requests that are non-compliant (using the default value audit will report violations but not block requests.)
1kubectl create -f- << EOF
2apiVersion: kyverno.io/v1
3kind: ClusterPolicy
4metadata:
5 name: require-labels
6spec:
7 validationFailureAction: enforce
8 rules:
9 - name: check-for-labels
10 match:
11 resources:
12 kinds:
13 - Pod
14 validate:
15 message: "label 'app.kubernetes.io/name' is required"
16 pattern:
17 metadata:
18 labels:
19 app.kubernetes.io/name: "?*"
20EOF
Try creating a Deployment without the required label:
1kubectl create deployment nginx --image=nginx
You should see an error:
1Error from server: admission webhook "nirmata.kyverno.resource.validating-webhook" denied the request:
2
3resource Deployment/default/nginx was blocked due to the following policies
4
5require-labels:
6 autogen-check-for-labels: 'Validation error: label `app.kubernetes.io/name` is required;
7 Validation rule autogen-check-for-labels failed at path /spec/template/metadata/labels/app.kubernetes.io/name/'
Note
Kyverno may be configured to exclude system namespaces likekube-system and the kyverno namespace. Make sure you run the test pod in a user defined namespace, or the default namespace.
Although the ClusterPolicy matches on Pods, Kyverno intelligently applies this to all sources capable of generating Pods by default, including the Deployment above.
Create a Pod with the required label. For example, using this command:
1kubectl run nginx --image nginx --labels app.kubernetes.io/name=nginx
This Pod configuration is compliant with the policy rules and is not blocked.
Congratulations, you’ve just implemented a policy in your Kubernetes cluster!
Clean up by deleting all cluster policies:
1kubectl delete cpol --all